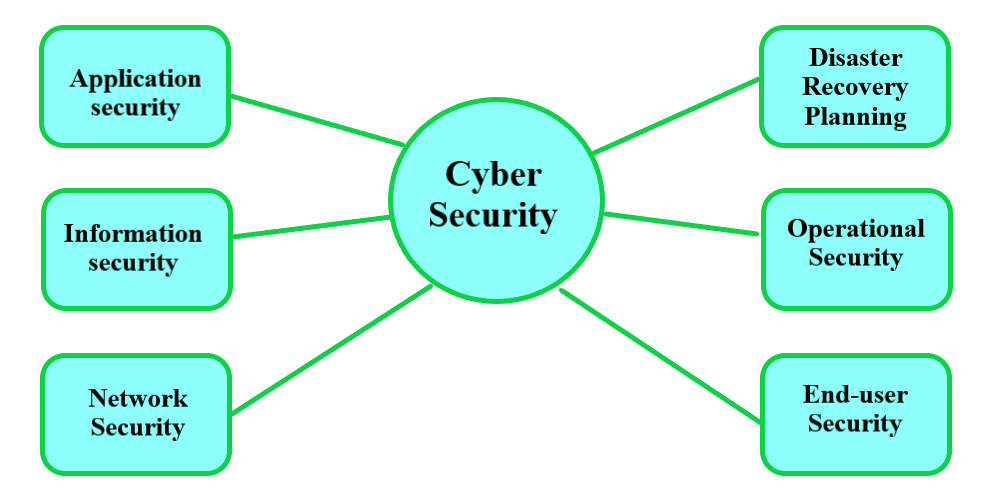
44 antivirus approaches in network security
What is Network Security? | Advantages | Scope & Skill - EDUCBA This security type also includes protecting files and servers against hacking and unauthorized changes in the networking system. An Antivirus system is the best example. Furthermore, protection involves protecting data from unauthorized personnel and protection against different activities from employees. Tech Paper: Endpoint Security, Antivirus, and Antimalware Best … WebNov 04, 2022 · Scan only local drives - or disable network scanning. The assumption is that all remote locations that might include file servers that host user profiles and redirected folders are being monitored by antivirus and data integrity solutions. If not, it is recommended that network shares accessed by all provisioned machines be excluded.
Difference between Antivirus and Internet Security - tutorialspoint.com In general, there are two main ways to viral detection − Dictionary Approach − When antivirus software scans a file, it automatically consults a virus dictionary. The file is removed, quarantined, or repaired if there is a match. Suspicious Behaviour Approach − Anti-virus software analyses all program behavior and flags any suspicious activity.
Antivirus approaches in network security
Cybersecurity Exchange | Cybersecurity Courses, Training ... WebJul 19, 2022 · What Is Virtual Network Security, and How Can It Help Thwart Threats? Network Security October 4, 2022. Read article. Why Your Next Career Move Should Be a Network Security Job. Network Security October 4, 2022. Read article. Load more. Penetration Testing. View All . Global Leader of Cyber Security Solutions and Services | Fortinet WebBy unifying Fortinet’s broad portfolio of zero trust, endpoint, and network security solutions, we can deliver security and services that automatically follow users across distributed networks. This enables consistent enterprise-grade … Fast flux - Wikipedia WebFast flux is a domain name system (DNS) based evasion technique used by cyber criminals to hide phishing and malware delivery websites behind an ever-changing network of compromised hosts acting as reverse proxies to the backend botnet master—a bulletproof autonomous systems. It can also refer to the combination of peer-to-peer networking, …
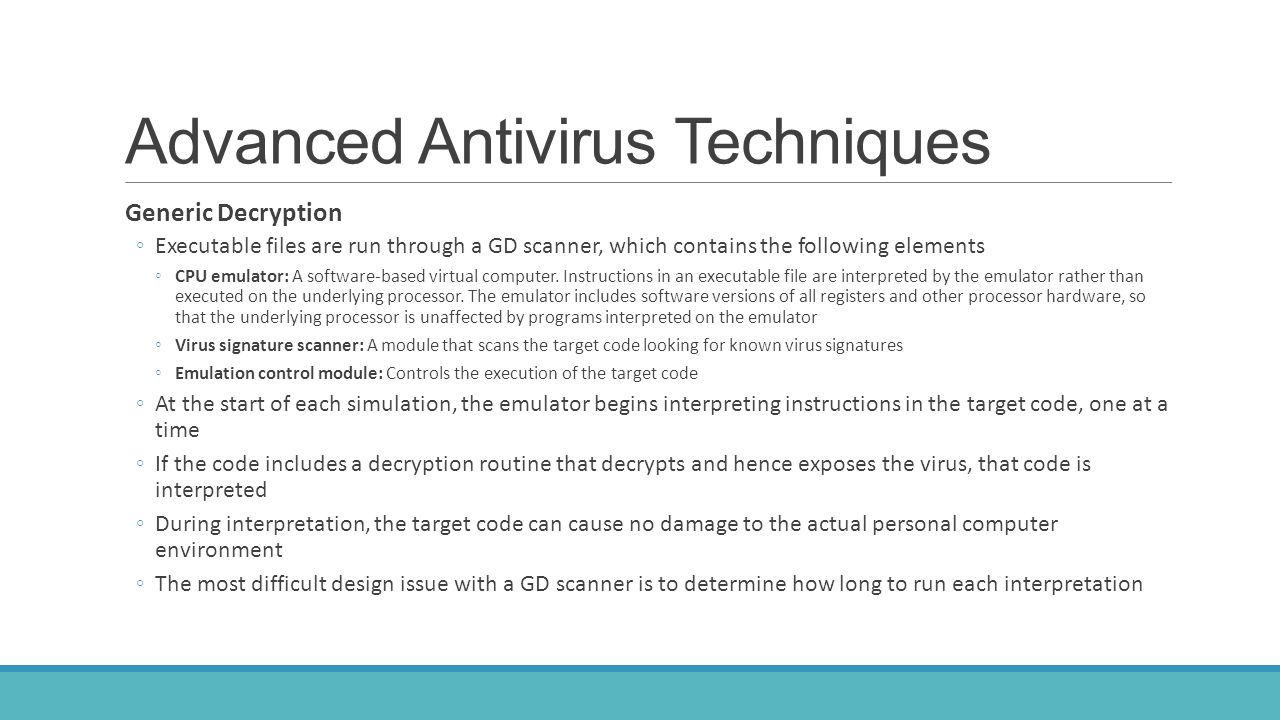
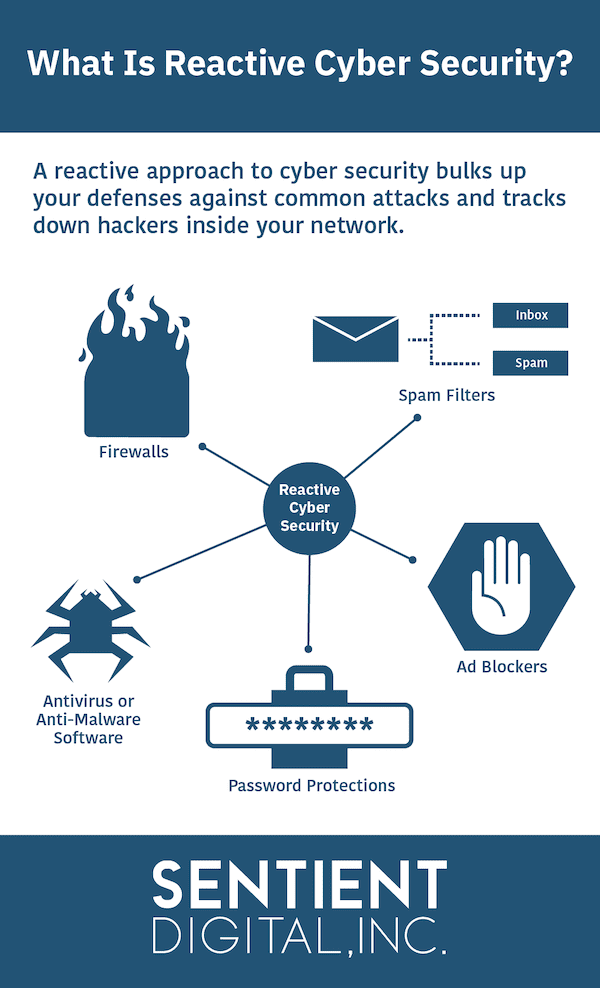
Antivirus approaches in network security. Section 19.2. Virus Countermeasures | Cryptography and Network Security ... Antivirus Approaches The ideal solution to the threat of viruses is prevention: Do not allow a virus to get into the system in the first place. This goal is, in general, impossible to achieve, although prevention can reduce the number of successful viral attacks. The next best approach is to be able to do the following: Network Security - GeeksforGeeks The basic principle of network security is protecting huge stored data and networks in layers that ensure the bedding of rules and regulations that have to be acknowledged before performing any activity on the data. These levels are: 1. Physical 2. Technical 3. Administrative These are explained as following below. Physical Network Security: What is Network Security? Types & Best Practices | CrowdStrike Network security is based on three main components: protection, detection and response. Protection Protection refers to any proactive security measures that the organization takes to prevent cyberattacks or other nefarious activity. This may include tools such as a next-gen antivirus (NGAV) or policies like privileged access management (PAM). docs.citrix.com › en-us › tech-zoneTech Paper: Endpoint Security, Antivirus, and Antimalware ... Nov 04, 2022 · Therefore, consultation with your vendor and your security team is recommended. Most antivirus vendors with solutions for virtualized environments offer optimized scanning engines. Antivirus Exclusions. The most common (and often the most important) optimization for antivirus is the proper definition of antivirus exclusions for all components.
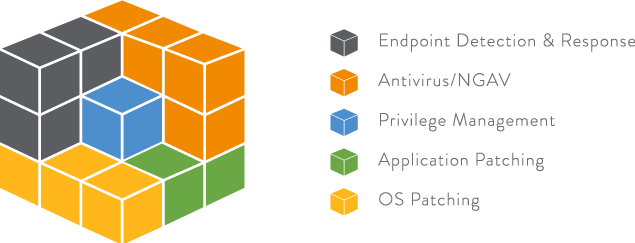
Network Security, Firewalls & Anti-Virus | Fusion Managed IT Next-generation firewalls (NGFWs) utilize purpose-built security processors and threat intelligence security services to deliver top-rated protection, intrusion prevention, and high-performance inspection of clear-text and encrypted traffic. Next-generation firewalls reduce cost and complexity with full visibility into applications, users, and networks, providing best-of-breed security. › antivirus › avast-vs-avgAvast vs AVG : Side-by-side Antivirus Review (2022) - Comparitech May 10, 2022 · Avast and AVG use different approaches to malware protection. My winner has to be Avast. Avast provides multi-layer protection and security, with an extensive feature list. Avast goes for the simple approach in terms of product offerings with just one paid option, making it easy for the consumer to understand what they’re getting. See also: Avast vs AVG : Side-by-side Antivirus Review (2022) - Comparitech WebMay 10, 2022 · BEST DEAL FOR AVAST: Get 70% off Avast Ultimate including all of its great security features and a VPN to protect your online activity. BEST DEAL FOR AVG: Save 70% on AVG Ultimate and protect up to 10 compatible devices. Background Avast. Based in Prague, Avast has more than 435 million active users. This makes it the second … Antivirus & Network Security - Advantech IT Solutions Our network security and antivirus services include but are not limited to: Enterprise antivirus deployment and management Secure firewall deployment and management Security awareness training for your employees DNS filtering deployment and management Office365 security assessments and management prev next CALL NOW AT (949) 427-6956
Two Approaches to Network Security - dummies When you're planning how to implement security on your network, you should first consider which of two basic approaches to security you will take: An open-door type of security, in which you grant everyone access to everything by default and then place restrictions just on those resources to which you want to limit access. What Is Network Security? - Cisco A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. Cisco offers both threat-focused firewalls and unified threat management (UTM) devices. Explore Cisco Secure Firewall Intrusion prevention systems Antivirus software - Wikipedia WebAntivirus software running on individual computers is the most common method employed of guarding against malware, but it is not the only solution. Other solutions can also be employed by users, including Unified Threat Management , hardware and network firewalls, Cloud-based antivirus and online scanners. Hardware and network firewall PlayStation userbase "significantly larger" than Xbox even if every … WebOct 12, 2022 · Microsoft has responded to a list of concerns regarding its ongoing $68bn attempt to buy Activision Blizzard, as raised by the UK's Competition and Markets Authority (CMA), and come up with an ...
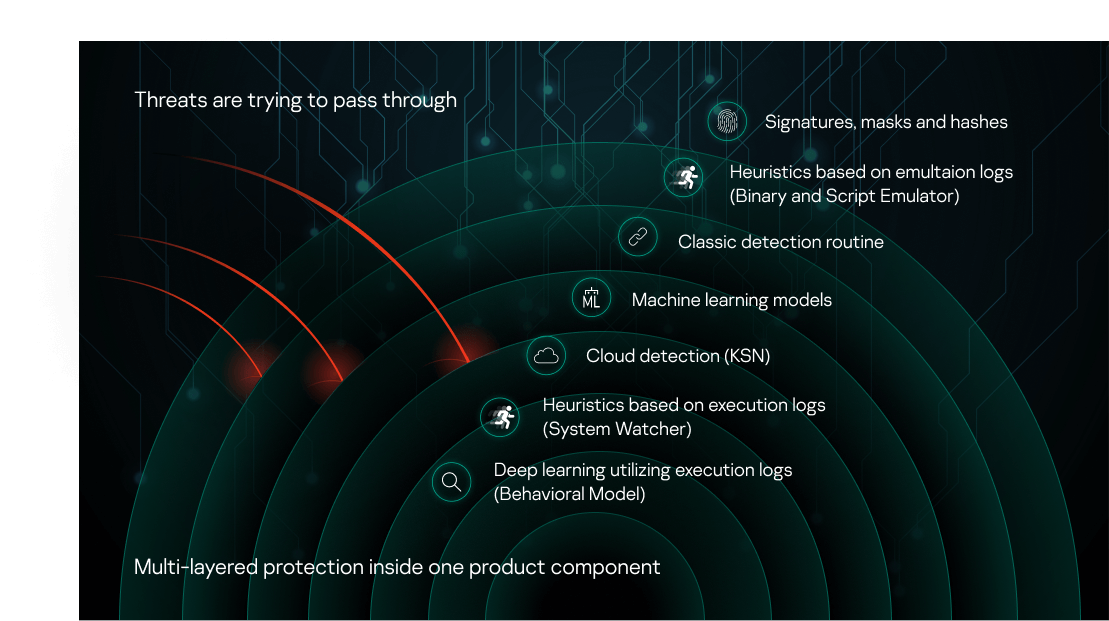
What is Layered Security & How Does it Defend Your Network? Layered security is a network security approach that deploys multiple security controls to protect the most vulnerable areas of your technology environment where a breach or cyberattack could occur. The purpose of a multi-layered security approach is to ensure that each individual component of your cybersecurity plan has a backup to counter any ...
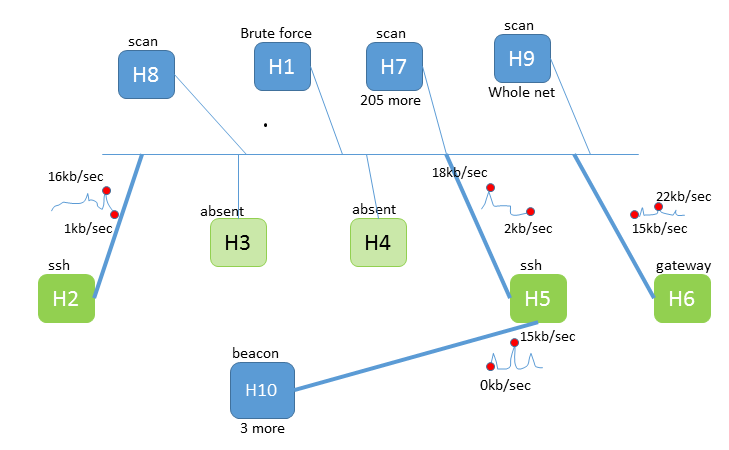
Advanced Approaches to ATM Network Protection - Security Intelligence To detect unsolicited ATM network access, bank security specialists should follow best practices, including: Installing a perimeter firewall to ensure a secure connection between the bank's...
› cybersecurity-exchangeCybersecurity Exchange | Cybersecurity Courses, Training ... Jul 19, 2022 · Gain exclusive access to cybersecurity news, articles, press releases, research, surveys, expert insights and all other things related to information security.
Network Security vs. Cybersecurity: Which Career Path to … WebAug 31, 2021 · These programs typically cover hardware and system security, data security, network security, cybersecurity policy development and the logistics of security. Some bachelor's degree programs focus wholly on cybersecurity, but most cover topics related to cybersecurity as part of the main computer science or in a concentration track.
Top Network Security Software 2022 | Features, Reviews, Pricing Network-level security vs. endpoint security: Most network security software approaches network security from a network perspective or from an endpoint perspective. If the network is on-premise, and any connected devices primarily remain within the network, then network-level security like firewalls and secure web gateways may be sufficient.
Best practices for network security - Microsoft Azure Azure network security appliances can deliver better security than what network-level controls provide. Network security capabilities of virtual network security appliances include: Firewalling Intrusion detection/intrusion prevention Vulnerability management Application control Network-based anomaly detection Web filtering Antivirus
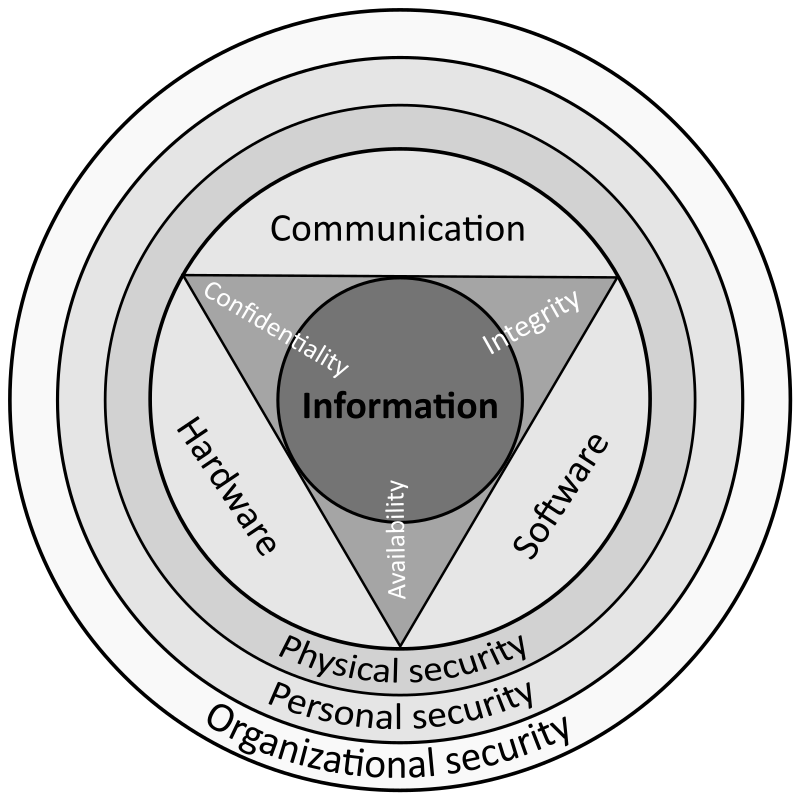
en.wikipedia.org › wiki › Information_securityInformation security - Wikipedia The CIA triad of confidentiality, integrity, and availability is at the heart of information security. ( The members of the classic InfoSec triad—confidentiality, integrity, and availability—are interchangeably referred to in the literature as security attributes, properties, security goals, fundamental aspects, information criteria, critical information characteristics and basic building ...
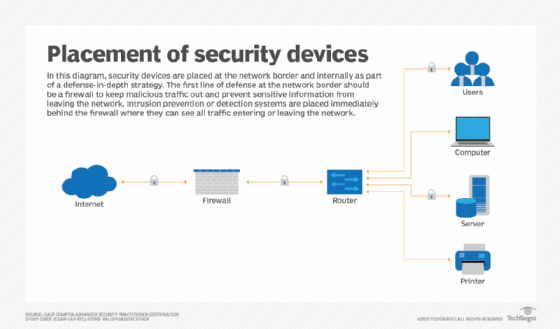
Network Security Best Practices Place Your Security Devices Correctly. As you design your network segregation strategy, you need to determine where to place all your devices. The easiest device to place is the firewall: You should place a firewall at every junction of a network zone. Each segment of your network should be protected by a firewall.
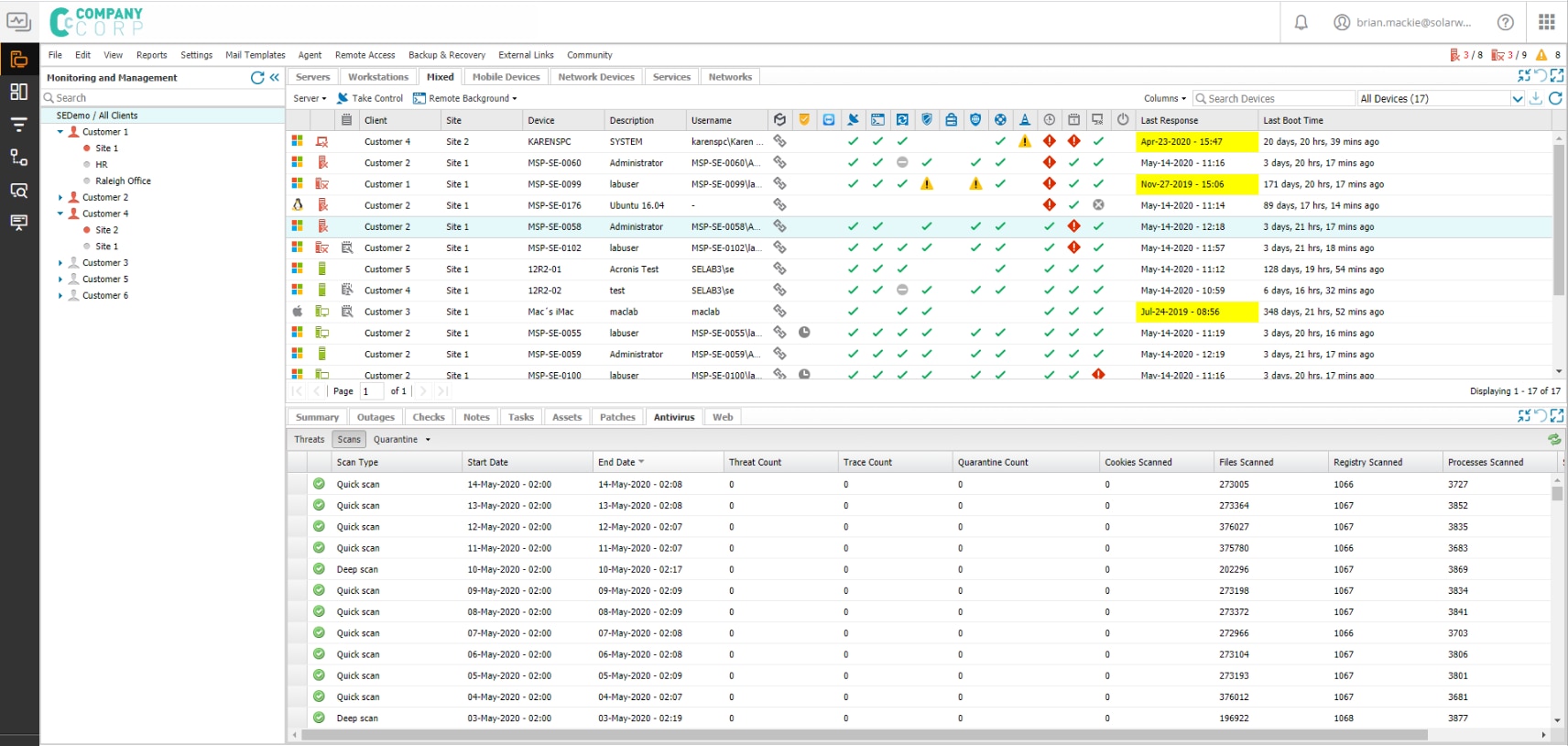
6 - Network Antivirus Protection THE FOLLOWING STEPS PROVIDE A HIGH DEGREE OF NETWORK PROTECTION Setting a limit on rights to download and install software Setting a limit on rights for users who use external networks Performing the timely installation and update of antivirus software Verifying software functionality Fixing bugs and errors that arise
Information security - Wikipedia WebComputer security software. Antivirus software; Security-focused operating system; Data-centric security ... The access control mechanism a system offers will be based upon one of three approaches to access control, or it may be derived from a combination of the three approaches. ... network security, etc. This team should also keep track of ...
Approaches of Network Security - Bitten Tech Solutions In a perimeter security approach, the bulk of security efforts are focused on the perimeter of the network. This focus might include firewalls, proxy servers, password policies, and any technology or procedure that makes unauthorised access of the network less likely. Little or no effort is made to secure the systems within the network.
Five Ways to Defend Against Network Security Threats Security policies can help ensure that all devices on a network are protected against viruses and malware and that users are using strong passwords. These policies can also restrict access to some network regions and limit user privileges. 4. Use firewalls. Firewalls are another essential tool in defending networks against security threats.
Network Security Devices: Effectiveness of Security Approaches The purpose of the study is to evaluate the effectiveness of security approaches to protect NFC services. Thus, the advantages and disadvantages of each of the most commonly used methods will be identified. Our experts can deliver a customized essay tailored to your instructions for only $13.00 $11.05/page 308 qualified specialists online
en.wikipedia.org › wiki › Antivirus_softwareAntivirus software - Wikipedia Antivirus software running on individual computers is the most common method employed of guarding against malware, but it is not the only solution. Other solutions can also be employed by users, including Unified Threat Management , hardware and network firewalls, Cloud-based antivirus and online scanners. Hardware and network firewall
Approaches In Network Security for Businesses Intrusion prevention systems. Wireless Security. Application Security. Access Control. Security approaches in network security. Level 1 - Minimal Protection. Level 2 - Advanced Protection. Level 3 - Maximal Protection. Summing it up.
lyleonline.smu.edu › blog › network-security-vsNetwork Security vs. Cybersecurity: Which Career Path ... - SMU Aug 31, 2021 · These programs typically cover hardware and system security, data security, network security, cybersecurity policy development and the logistics of security. Some bachelor's degree programs focus wholly on cybersecurity, but most cover topics related to cybersecurity as part of the main computer science or in a concentration track.
Network Antivirus | Sophos Advanced Security with XDR, MDR Sophos antivirus protection for networks is built to stop ransomware, viruses, and advanced malware attacks in their tracks. Combining the industry's leading malware detection with XDR security and MDR services, Sophos will future-proof your organization against both new and old threats. Endpoint Security Sophos MDR Server Protection
› playstation-userbasePlayStation userbase "significantly larger" than Xbox even if ... Oct 12, 2022 · Microsoft has responded to a list of concerns regarding its ongoing $68bn attempt to buy Activision Blizzard, as raised by the UK's Competition and Markets Authority (CMA), and come up with an ...
U.S. appeals court says CFPB funding is unconstitutional - Protocol WebOct 20, 2022 · That means the impact could spread far beyond the agency’s payday lending rule. "The holding will call into question many other regulations that protect consumers with respect to credit cards, bank accounts, mortgage loans, debt collection, credit reports, and identity theft," tweeted Chris Peterson, a former enforcement attorney at the CFPB who is …
Protection Methods for Network Security - GeeksforGeeks Firewall : A firewall is a method of network security that prevents the computer network from users that are not authorized to have access to a network. Firewalls can either be hardware or software or both. It acts as a barrier between unauthorized Internet users and private computer networks connected to the Internet.
Fast flux - Wikipedia WebFast flux is a domain name system (DNS) based evasion technique used by cyber criminals to hide phishing and malware delivery websites behind an ever-changing network of compromised hosts acting as reverse proxies to the backend botnet master—a bulletproof autonomous systems. It can also refer to the combination of peer-to-peer networking, …
Global Leader of Cyber Security Solutions and Services | Fortinet WebBy unifying Fortinet’s broad portfolio of zero trust, endpoint, and network security solutions, we can deliver security and services that automatically follow users across distributed networks. This enables consistent enterprise-grade …

Webroot Internet Security Plus | Antivirus Software 2023 |3 Device|1 Year Keycard Delivery for PC/Mac/Chromebook/Android/IOS + Password Manager
Cybersecurity Exchange | Cybersecurity Courses, Training ... WebJul 19, 2022 · What Is Virtual Network Security, and How Can It Help Thwart Threats? Network Security October 4, 2022. Read article. Why Your Next Career Move Should Be a Network Security Job. Network Security October 4, 2022. Read article. Load more. Penetration Testing. View All .



























0 Response to "44 antivirus approaches in network security"
Post a Comment